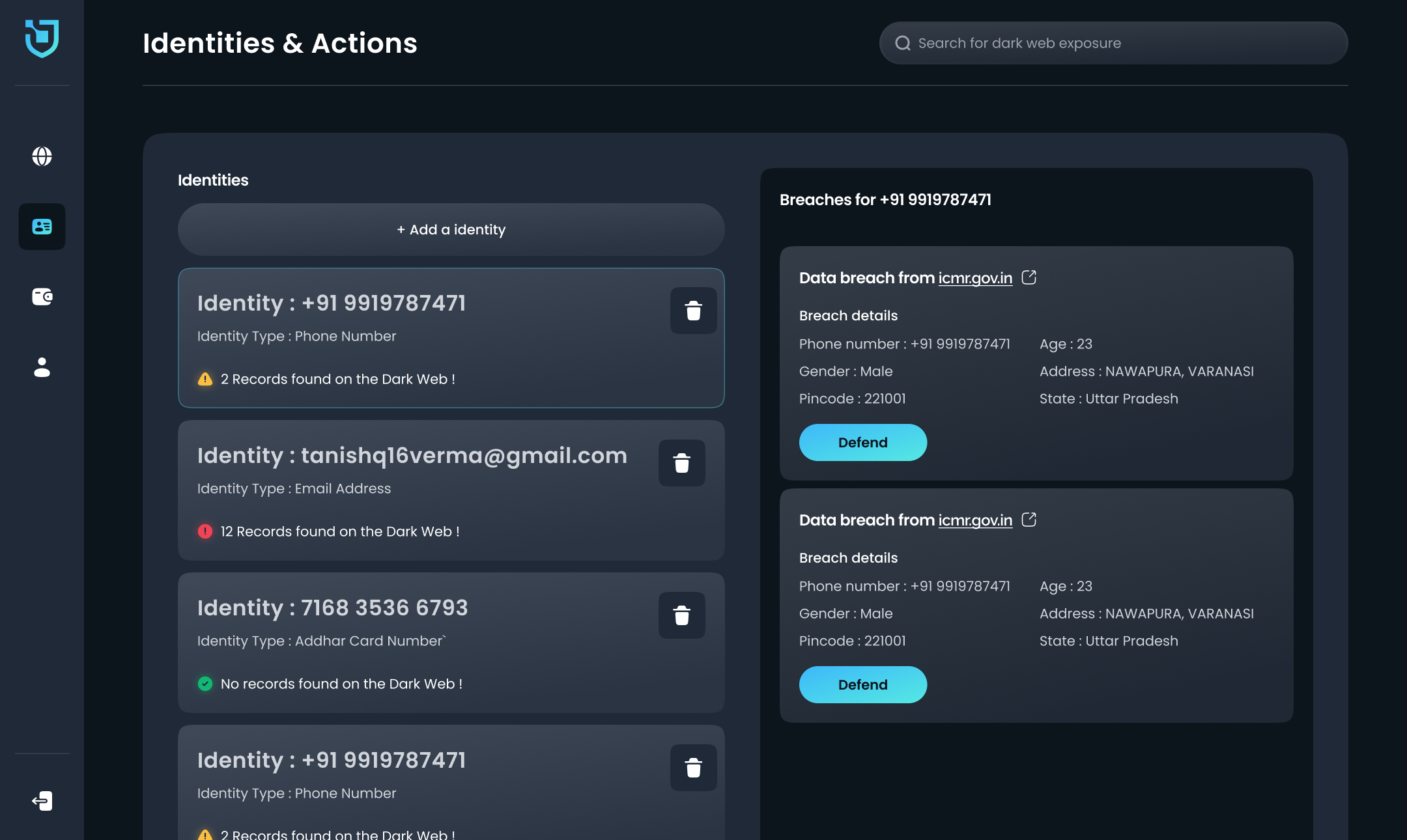
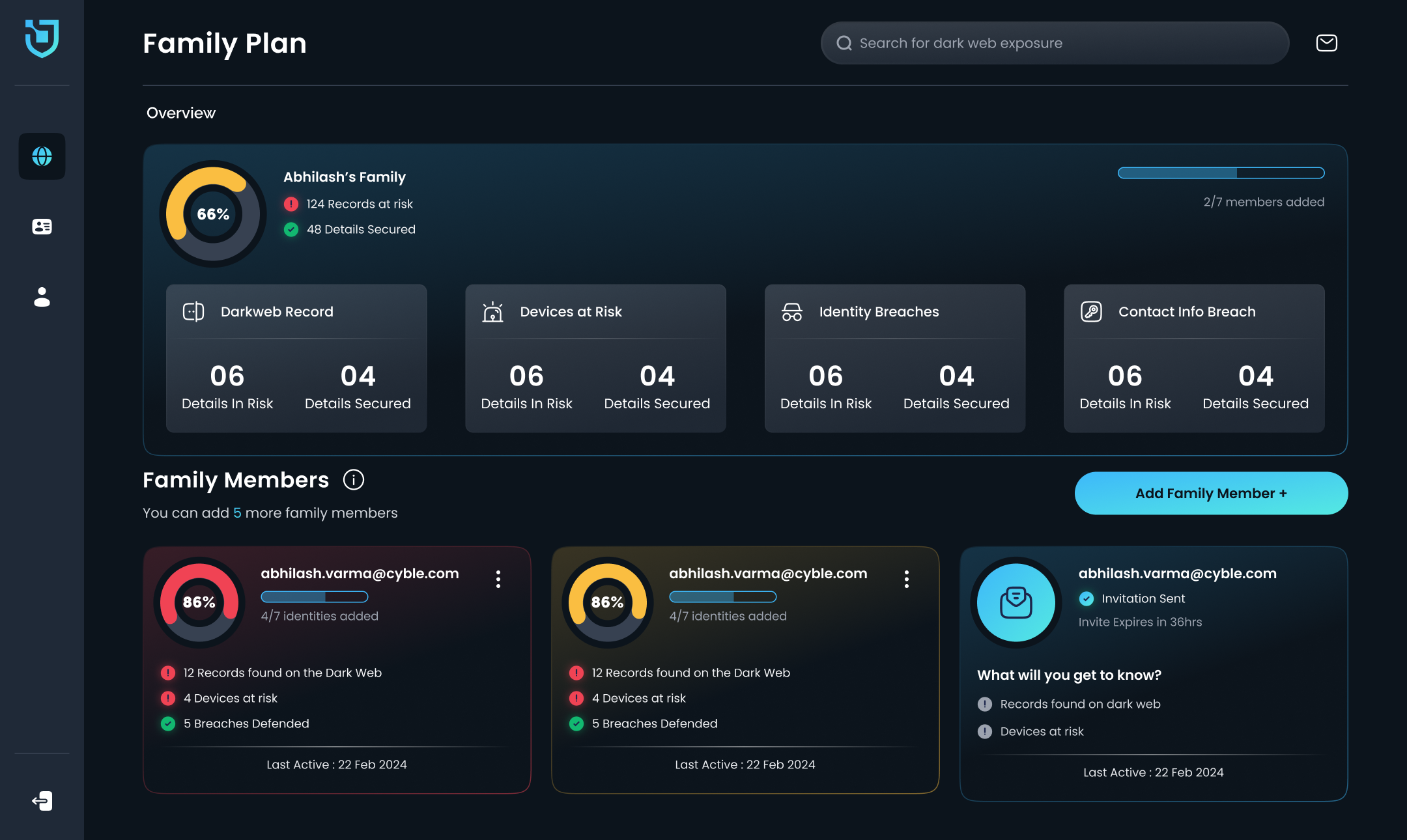
AmIBreached - Search for your dark web exposure
A Brief Introduction
AmIBreached.com is a free, user-focused cybersecurity tool that allows individuals to quickly and securely check whether their email address has been involved in any known data breaches. The platform is designed with simplicity, trust, and clarity at its core—empowering users to take immediate action to protect their personal information online. By entering an email address, users receive instant feedback about breach exposure, along with actionable next steps like changing compromised passwords and enhancing account security. The product serves as a crucial first line of defense in a digital landscape where data leaks and cyber threats are increasingly common.
-
Website
Problem Statement
Users are increasingly concerned about the security of their personal data online, but many lack a quick, trustworthy, and user-friendly way to check if their email or phone number has been compromised in data breaches. Existing solutions can feel overwhelming, untrustworthy, or too technical—creating friction and hesitation in taking proactive steps.
As a UX designer, the challenge is to design a simple, intuitive, and secure platform that allows users to effortlessly check for breaches, understand the implications, and take action—without compromising their sense of privacy or digital safety.
1. Research Phase
A. Primary Research
we conducted qualitative and observational primary research. Our focus was to uncover user behavior, motivations, and pain points while interacting with breach-checking tools
Research Objectives
- Understand how users currently check for data breaches
- Identify emotional and cognitive responses to breach notifications
- Test user trust levels and clarity of security information
- Evaluate how users interpret and act upon breach results
- Assess the usability of the initial design flow (desktop & mobile)
Methods Used
-
Methods1:1 User InterviewsThink-Aloud Usability TestIn-Person ObservationsSurvey (Google Forms)
-
PurposeDiscover motivations, habits, mental modelsCapture real-time reactions and friction pointsObserve body language and non-verbal cues during interactionCollect scalable insights from 30+ users about privacy and breach tools
Participant Demographics
We interviewed and tested with 10 participants and surveyed 32 users from these target groups:
- Age: 20–38
- Occupation: Students, early-career professionals, small business owners
- Location: India, UK, and Australia
- Device usage: 70% Mobile-first, 30% Desktop-first
- Digital literacy: Mixed (from basic users to cybersecurity-aware professionals)
Key Insights from Interviews & Testing
- Mental Modal Gaps
“I thought this would tell me if my phone is being tracked—I didn’t expect breach history.”- Users misunderstood what a “breach check” tool actually does.
- Terms like “breach,” “leak,” and “exposed” caused confusion.
Design Fix: We addedtooltips and simple definitionsnext to the search field and in results, e.g.“A breach means your data was found in a publicly leaked database.”
- Trust & Anxiety
“Why would I enter my email here? What if this site is fake?”- Many users were hesitant to enter sensitive information.
- Trust was impacted by minimal branding or lack of familiar trust signals.
- Design Fix:
- Introduced trust badges (e.g., “We don’t store your data”, SSL lock, GDPR compliant).
- Simplified layout with clean white space and reduced dark-pattern elements.
- Added an “About Us” page to establish credibility.
- Attention Span & Feedback
“I clicked check, but nothing happened. Is it working?”- Users expected immediate visual confirmation after hitting “Check”.
- A few users clicked multiple times due to lack of feedback.
- Design Fix:
- Implemented microinteractions (loading animation, button state change).
- Added color-coded results with icons and friendly, direct text.
- User Flow Improvements
“Do I need to press back and try again if I want to search another email?”- Navigation was confusing after a result was shown.
- Users wanted to do multiple checks without refreshing the page.
- Design Fix:
- Introduced a persistent search bar above the results.
- Allowed easy switching between email and phone lookup using toggle tabs.
- Desire for Guidance
“Okay I’ve been breached. Now what?”- Users felt overwhelmed or unsure how to respond to breaches.
- Some assumed that the site would automatically fix the issue.
- Design Fix:
- Added a “Next Steps” guide with 3 simple actions:
- Change your password
- Use a password manager
- Monitor accounts for unusual activity
- Linked to educational blog content for deeper security learning
B. Secondary Research
We conducted extensive secondary research to understand the landscape of cybersecurity awareness, user behaviors, and market gaps in breach-checking tools. The research informed the product direction, helped define user personas, and guided our UX principles.
- Industry Trend Analysis
We analyzed reports and whitepapers from trusted cybersecurity sources like IBM Security, Norton, and Google to understand rising threats and user needs.
Key Insights
- 91% of users feel they’ve lost control over how personal data is collected and used (Pew Research).
- The number of reported data breaches worldwide rose by 78% in the past two years (IBM X-Force Threat Intelligence).
- Mobile-first security tools are in high demand, especially in countries like India and Southeast Asia, where internet access is primarily mobile.
Impact on Design: We prioritized a mobile-responsive, minimal-step design to reduce barriers for non-technical users and built trust by clearly stating that data entered is not stored or reused.
- Competitor Feature Mapping
We did competitor reviews to find out what is missing in them and how can we provide ore intutive services to our customers through our product.
We audited major players such as:
- Have I Been Pwned
- Firefox Monitor
- DeHashed
- LeakCheck.io
Evaluation Criteria:
- Information architecture and user flow
- Types of data supported (email, phone, domain, etc.)
- Trust signals (SSL, non-storage policies, about pages)
- Result explanation clarity
- UX writing tone and visual feedback styles
Key Findings:
- Many breach-check tools are too technical or have cluttered interfaces.
- HIBP remains the leader but hasn’t updated its design significantly.
- Most tools fail to clearly guide what users should do after a breach.
- Phone number support is rare but increasingly important with rise in SMS spam and OTP leaks.
Impact on Design: We introduced support for both email and phone number checks on the same screen with a clean, trust-driven layout and actionable language like “You’re Safe” or “Take Action Now.”
- User Behavior Reports & Surveys
We analyzed survey data from Norton’s Cyber Safety Pulse and Google’s Safer Internet Day reports.
Key Findings:
- Over 60% of users reuse passwords across platforms despite knowing the risks.
- A large number of users don’t know what a data breach actually means.
- Skepticism is high when asked to enter personal info on lesser-known websites.
- Clear copywriting and visual feedback (e.g., color-coded results) improve user understanding and emotional response.
Impact on Design: We simplified messaging by using green for “no breach”, red for “breach found”, and short, jargon-free explanations. Also included a “What to do next” guide for breached users.
- Legal & Ethical Framework Review
We reviewed GDPR, India’s Digital Personal Data Protection Act (DPDPA), and CCPA (California) to ensure legal compliance and ethical design.
Key Takeaways:
- Tools must avoid storing or processing PII (personally identifiable information) unless necessary.
- Must disclose privacy policies upfront and in plain language.
- Consent should be implied only when no data is being retained or shared.
Impact on Design: No tracking or saving of user input was implemented. Disclaimer and privacy policy links were made visible upfront, reinforcing transparency.
- SEO & Keyword Behavior Research
We explored Google Trends and AnswerThePublic.com to identify how users search for breach-check tools.
Top Queries:
- “Check if my email was hacked”
- “Is my phone number leaked?”
- “Free breach checker no login”
- “How to know if my data was exposed”
Impact on Design: We designed the homepage to reflect SEO-friendly language without disrupting UX. Meta descriptions, H1 headers, and button CTAs match common search queries.
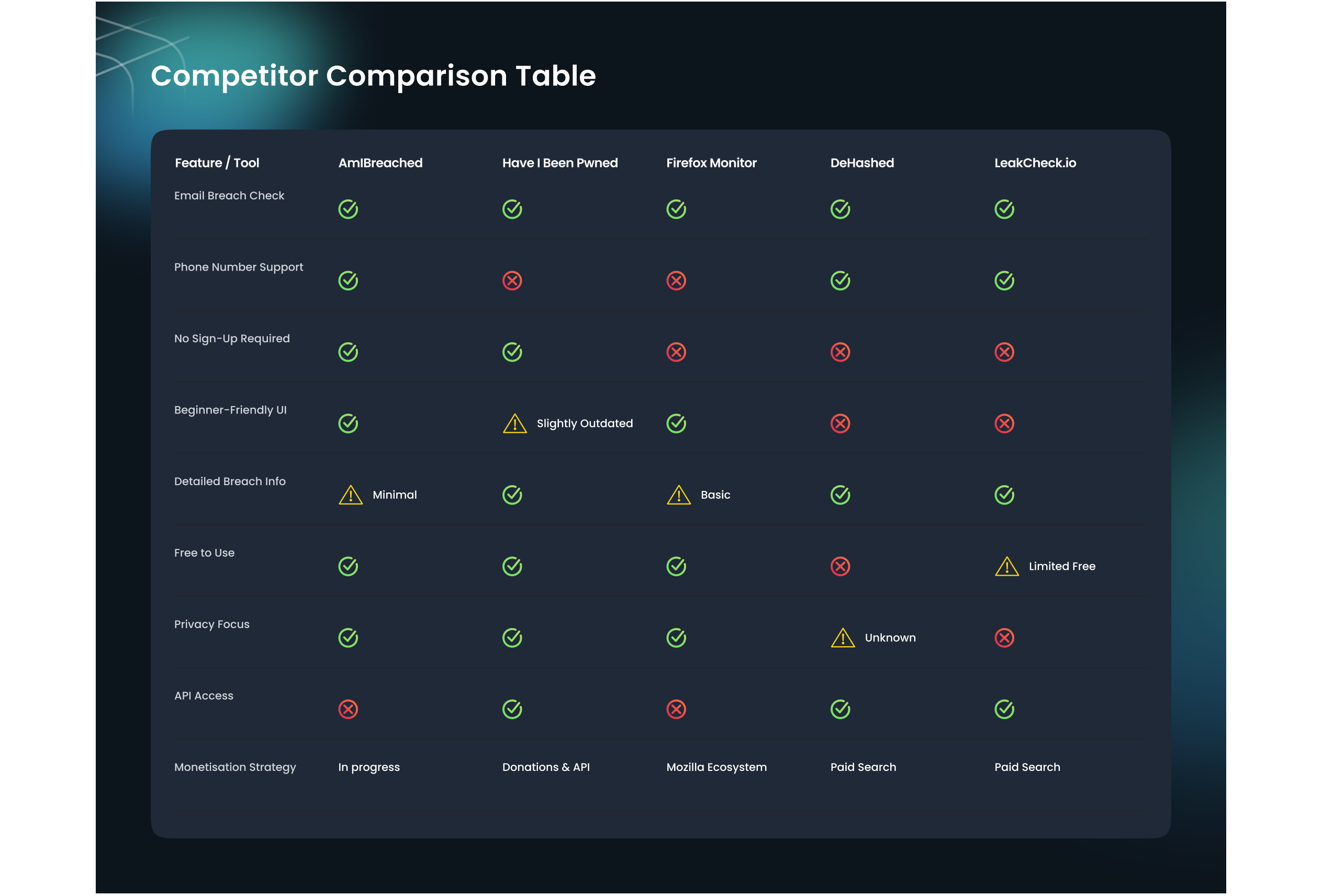
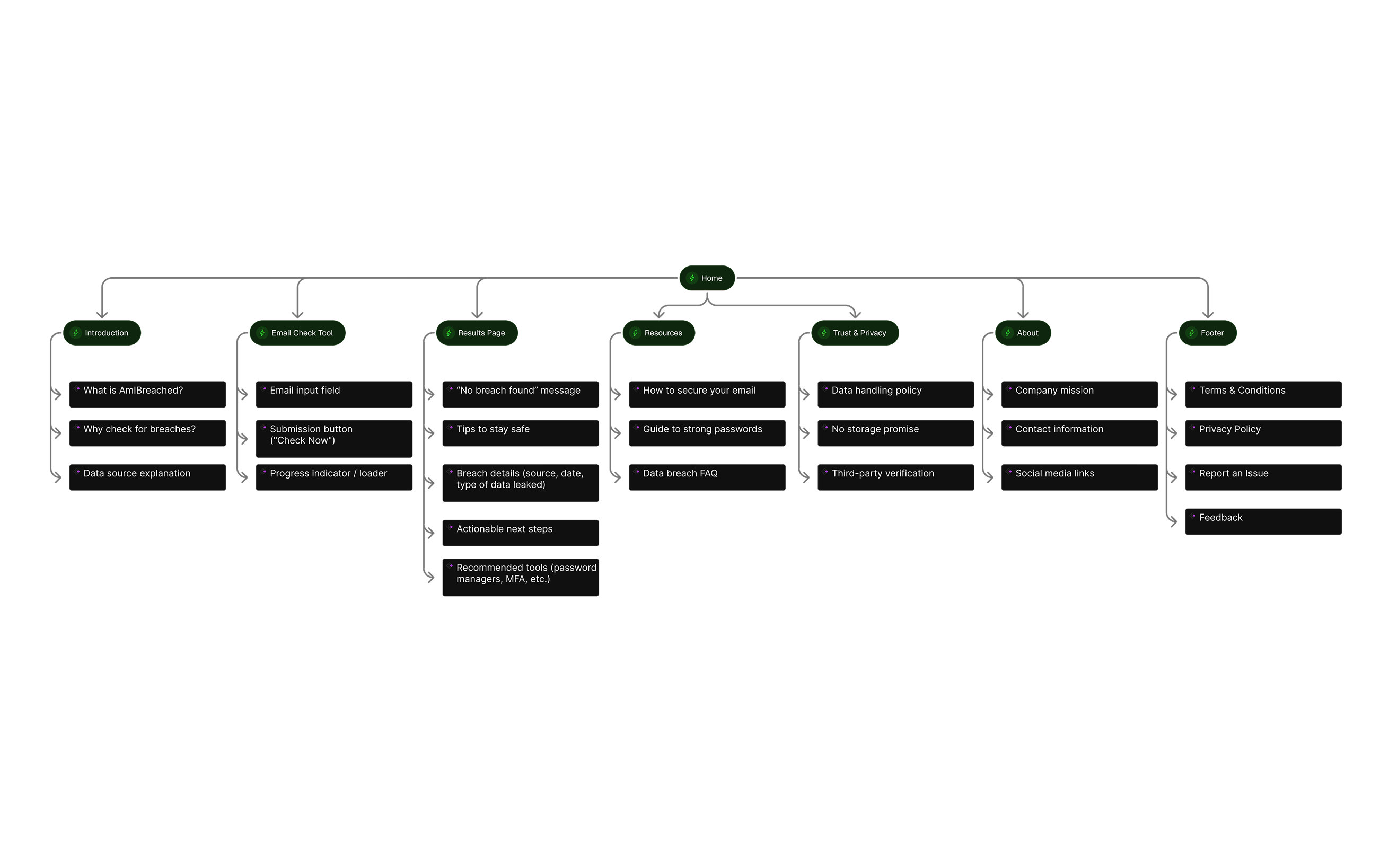
Competitor Analysis
Here are four key competitors in the data breach awareness space and how AmIBreached.com compares to each:
1. Have I Been Pwned (HIBP)
-
Strengths:Most well-known breach checking tool globallyMassive breach databaseAllows domain monitoring for companiesOpen API for developers
-
Weaknesses:Slightly outdated UI/UXHeavy reliance on email (no phone lookup in many regions)Results can be technical for non-expertsLess guidance on post-breach actions
2. Firefox Monitor
-
Strengths:Powered by HIBP databaseIntegrated with Firefox browserClean and simple designOffers breach alerts if you sign up
-
Weaknesses:Requires Mozilla account for full featuresLimited brand recognition outside Firefox usersNo phone number supportNo detailed breach breakdown
3. DeHashed
-
Strengths:Searches usernames, IPs, names, emails, domains, etc.Powerful for investigators or cybersecurity prosAPI and bulk search options
-
Weaknesses:Very complex interface—intimidating for casual usersPaid service for deep searchData overload—lacks user-friendlinessPrimarily B2B-focused
4. LeakCheck.io
-
Strengths:Multi-type search (email, IP, phone, etc.)Offers paid API and report generationUpdated frequently
-
Weaknesses:Requires credits or payment for full detailsNot beginner-friendlyQuestionable trust due to lack of transparency on sourcesMinimal design and usability investment
Business Impact Analysis
Here’s how AmIBreached.com contributes value across business dimensions:
- User Acquisition & Engagement
- Low-friction entry point builds immediate trust
- Shareable via social media, increasing organic reach
- High utility means users return to recheck their info
- Builds brand reputation through simplicity and speed
- Brand Authority in Cybersecurity
- Acts as a trust anchor for any cybersecurity brand it’s linked with
- Users view the brand as a protector of digital identity
- Opportunity to expand into thought leadership (e.g., blog, alerts, infographics)
- Can be used as an entry-point for upselling to privacy tools
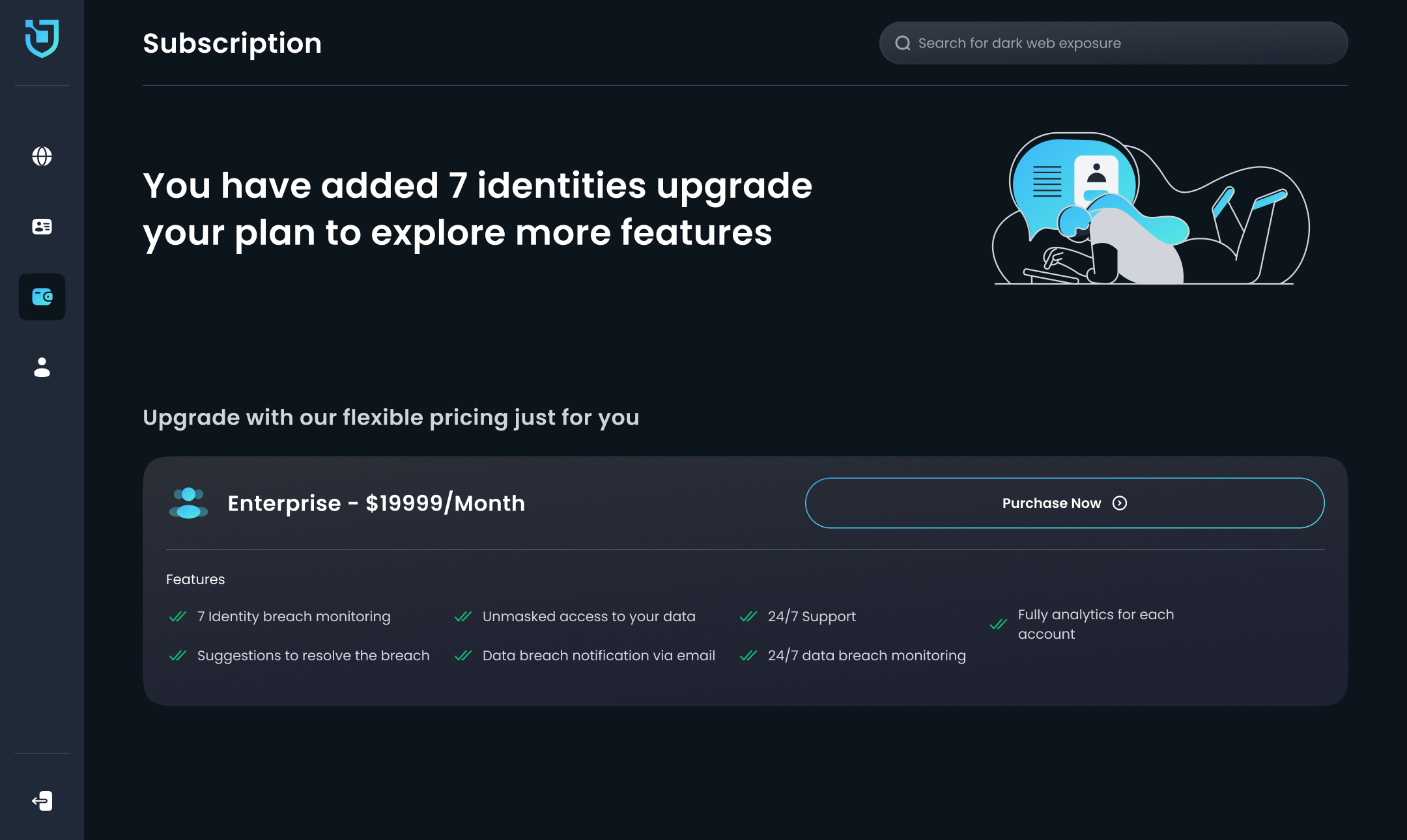
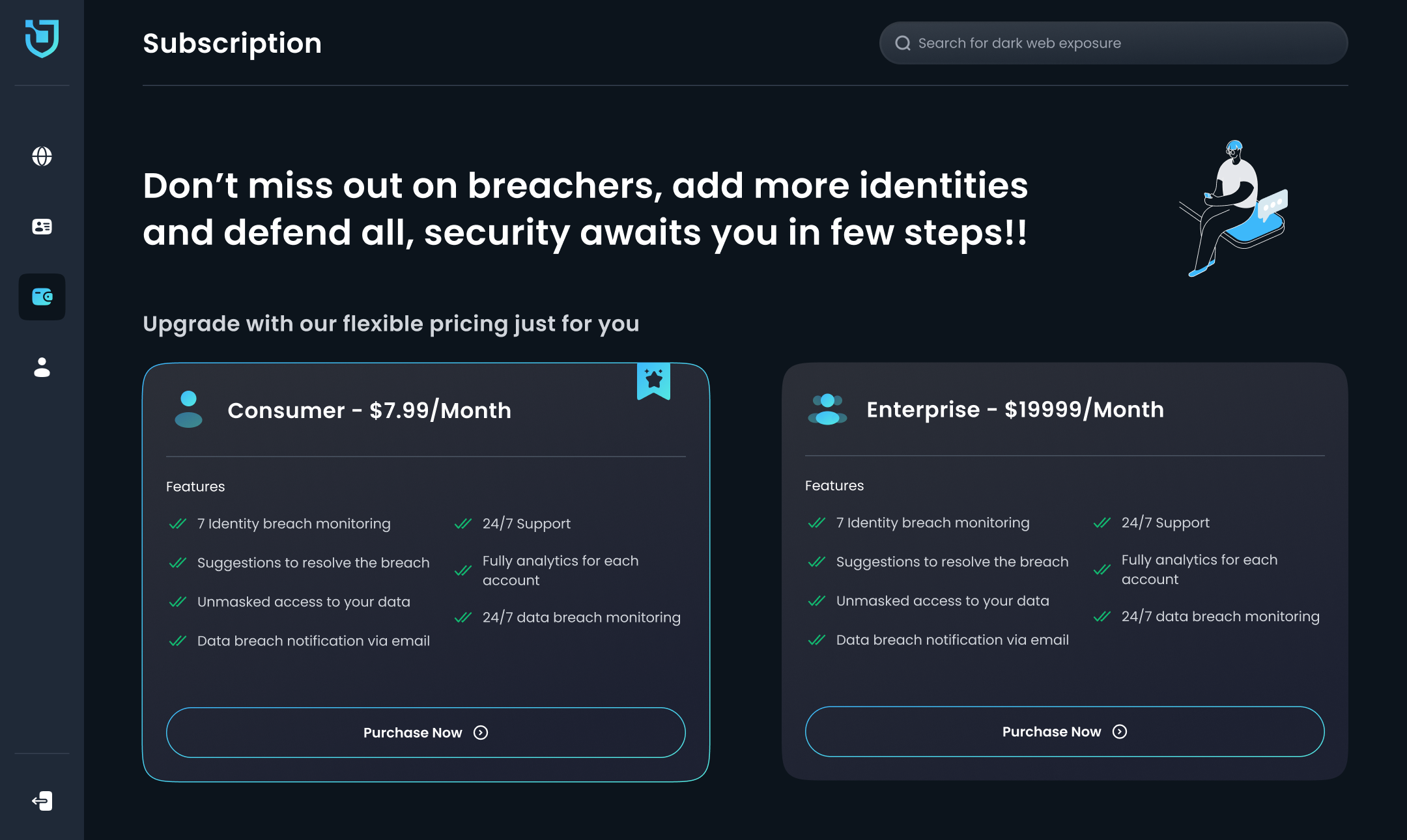
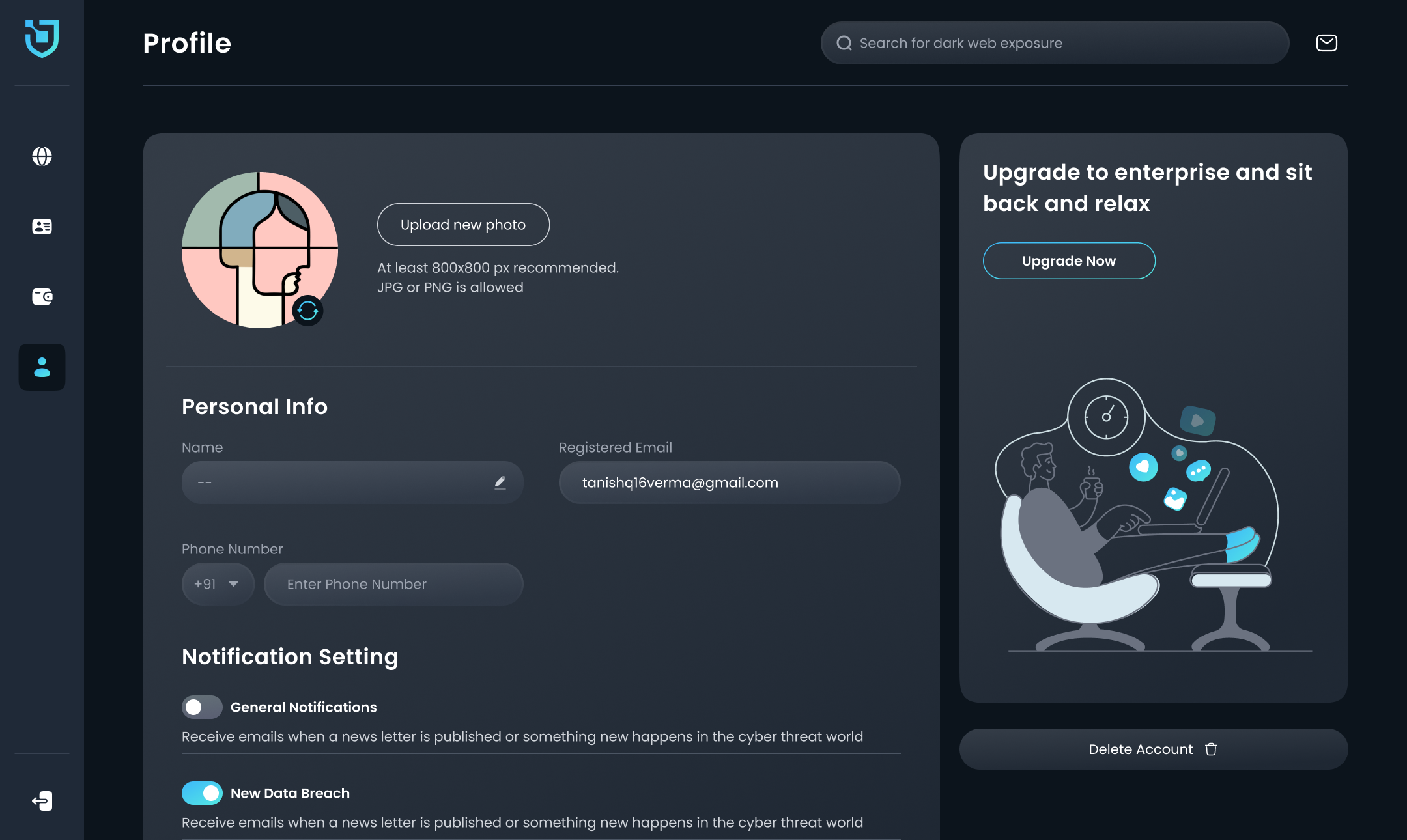
- Monetization Potential
- Can plug into affiliate products: VPNs, identity protection, password managers
- White-label opportunities for enterprises or SaaS integration
- Tiered offerings (free vs. pro breach monitoring tools)
- Sponsored content or partner programs for security education
- Market Differentiation
- Fills a UX gap in an otherwise technical market
- Focused on emerging markets (e.g., India) where awareness is rising
- Offers faster, lighter experience compared to bloated tools
- Aligns with privacy-first, no-login trend growing among Gen Z and millennials
- Data & Insights
- Breach trends
- Geographical patterns
- User behavior analytics
- Valuable for improving the platform and informing external partnerships
- Aggregate data (without storing personally identifiable info) can
provide:
Affinity Diagram
We grouped all insights into 4 main categories based on shared patterns:
User Understanding, Trust & Privacy, Usability & Flow, Actionability & Support>
User Understanding & Mental Models
- Many users didn't understand what "breach" actually means - User Interviews
- Confused between terms like leak, breach, and hack - User Testing
- Expected to check if their phone was "currently being tracked" - Usability test
- SEO trends show users searching for "Was my email hacked?" instead of "breach" - User Interviews
- Misconception that breach check tools auto-fix the issue - Interviews
Trust, Privacy & Security Concerns
- Users hesitant to enter email/phone without knowing the site's legitimacy - User Interviews
- Trusted sources like HIBP are favored due to reputation - Competitor Analysis
- Users want visible signs of credibility (SSL lock, About page, disclaimers) - Interviews & Survey
- Privacy-first messaging builds emotional safety - Industry Reports
- People prefer not creating accounts for simple security tools - Survey & Trends
Usability & Navigation
- Users didn't realize their search had been submitted - no feedback - Usability Test
- Multiple users clicked the "Check" button repeatedly - Think-Aloud Sessions
- Poor discoverability for repeat searches (no persistent search bar) - User Testing
- Competitor tools often cluttered or overly technical - Competitor Review
- Mobile-first design is essential for accessibility and global usage - Trend Analysis
Actionability & Post-Breach Support
- Most users asked: "Okay, now what?" after finding their email was breached - User Interviews
- Users expected help, not just results - Interviews & Testing
- Secondary research showed lack of post-breach guidance in most tools - Competitor Research
- Content-based education can enhance security behavior - Industry Reports
- People prefer step-by-step guidance vs overwhelming security jargon - Survey
Design Opportunity: Simplify terminology, include definitions, and educate users on what a breach is and isn’t.
Design Opportunity: Add trust indicators, clarify privacy policy, and emphasize “no data is stored.”
Design Opportunity: Add microinteractions, persistent search, improve button feedback, mobile responsiveness.
Design Opportunity: Add “What to do next” section, recommend tools (password managers), and link to learning resources.
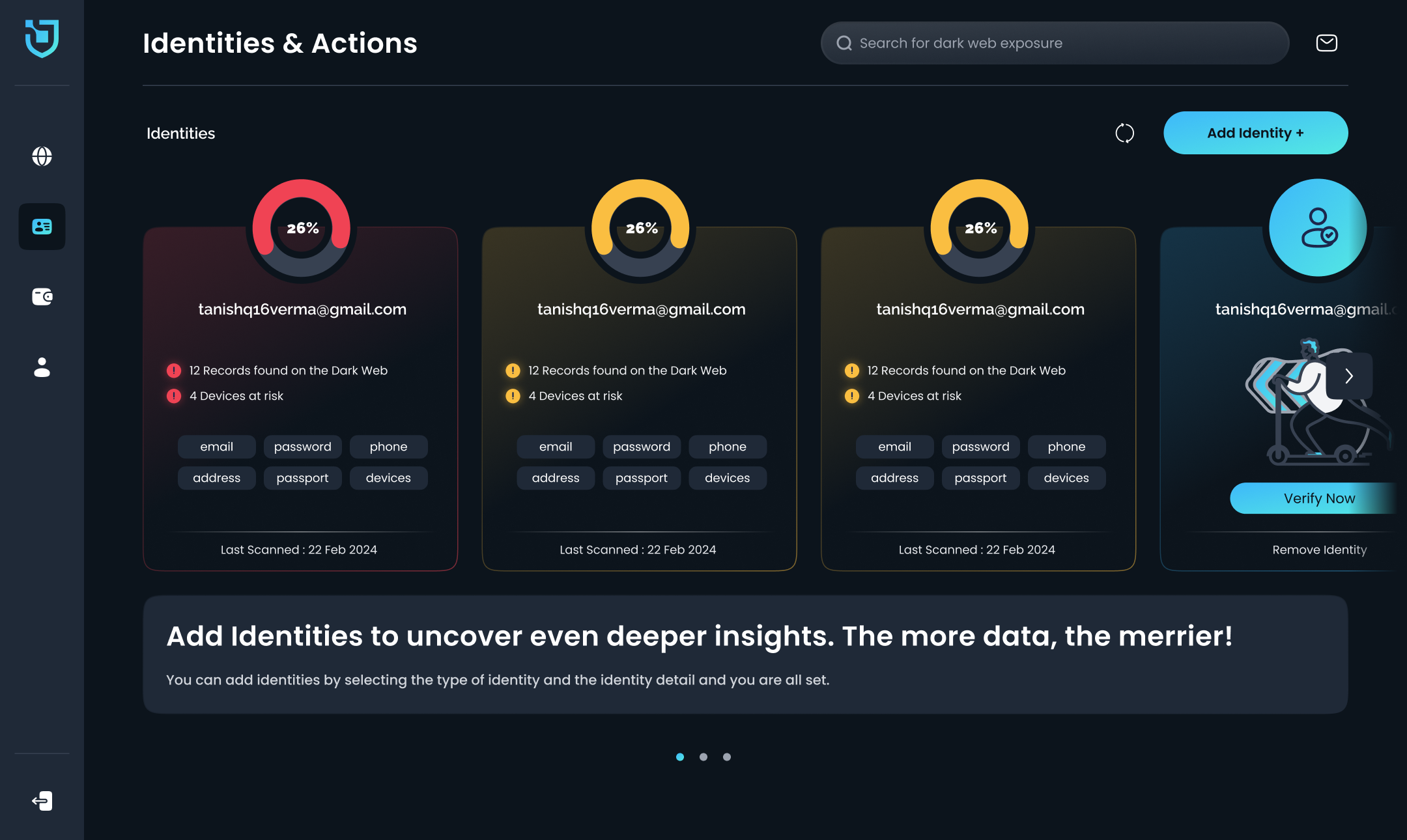
User Persona 1
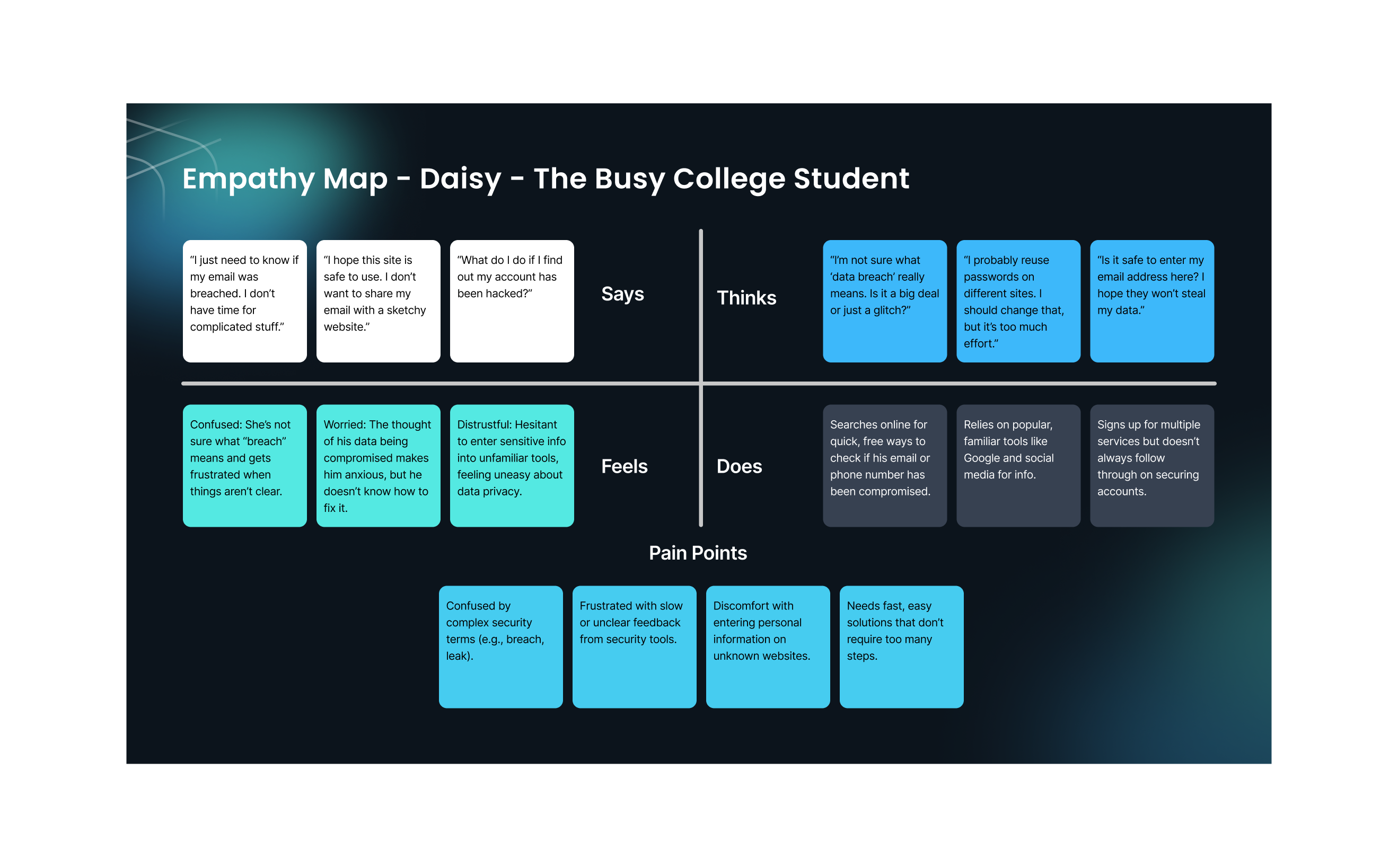
Daisy The Busy College Student

Basic Info:
- Name: Daisy
- Age: 24
- Occupation: Postgraduate Student (Computer Science)
- Location: Manchester, UK
- Tech Proficiency: Intermediate (Uses tech daily for study, social media, and research)
Background:
Daisy is a postgraduate student living in a shared flat with roommates. She is tech-savvy but not deeply involved in cybersecurity. While she understands basic online safety, she often forgets to change passwords and reuse them across multiple platforms. Daisy is busy balancing her academics, part-time job, and social life, making it hard for her to stay on top of security measures.
Goals:
- Simple and quick security checks without extra steps or technical jargon.
- No hassle for entering personal information—prefers tools that don’t require sign-ups or logins.
- To know whether his email and phone number have been breached in data leaks, so he can take preventive measures.
Pain Points:
- Doesn’t want to waste time on complex security tools: He needs something fast and efficient that doesn’t interrupt his day.
- Confusion around security terminology: Terms like “breach,” “leak,” and “hack” are often unclear to him, especially when he’s in a rush.
- Distrust of new websites: He’s hesitant to enter personal details unless the tool is widely known and trusted.
Technology Use:
- Device Preference: Primarily mobile (80%) and desktop (20%).
- App Usage: Frequent user of social media, emails, and shopping apps. Moderate user of banking and online learning platforms.
- Distrust of new websites: He’s hesitant to enter personal details unless the tool is widely known and trusted.
Behavioral Traits:
- Frequently checks his emails and social media for updates.
- Needs quick, digestible information on online security.
- Relies on Google searches for troubleshooting and solutions.
- Usually does not follow through with long-term security measures unless something immediate forces action.
User Persona 2
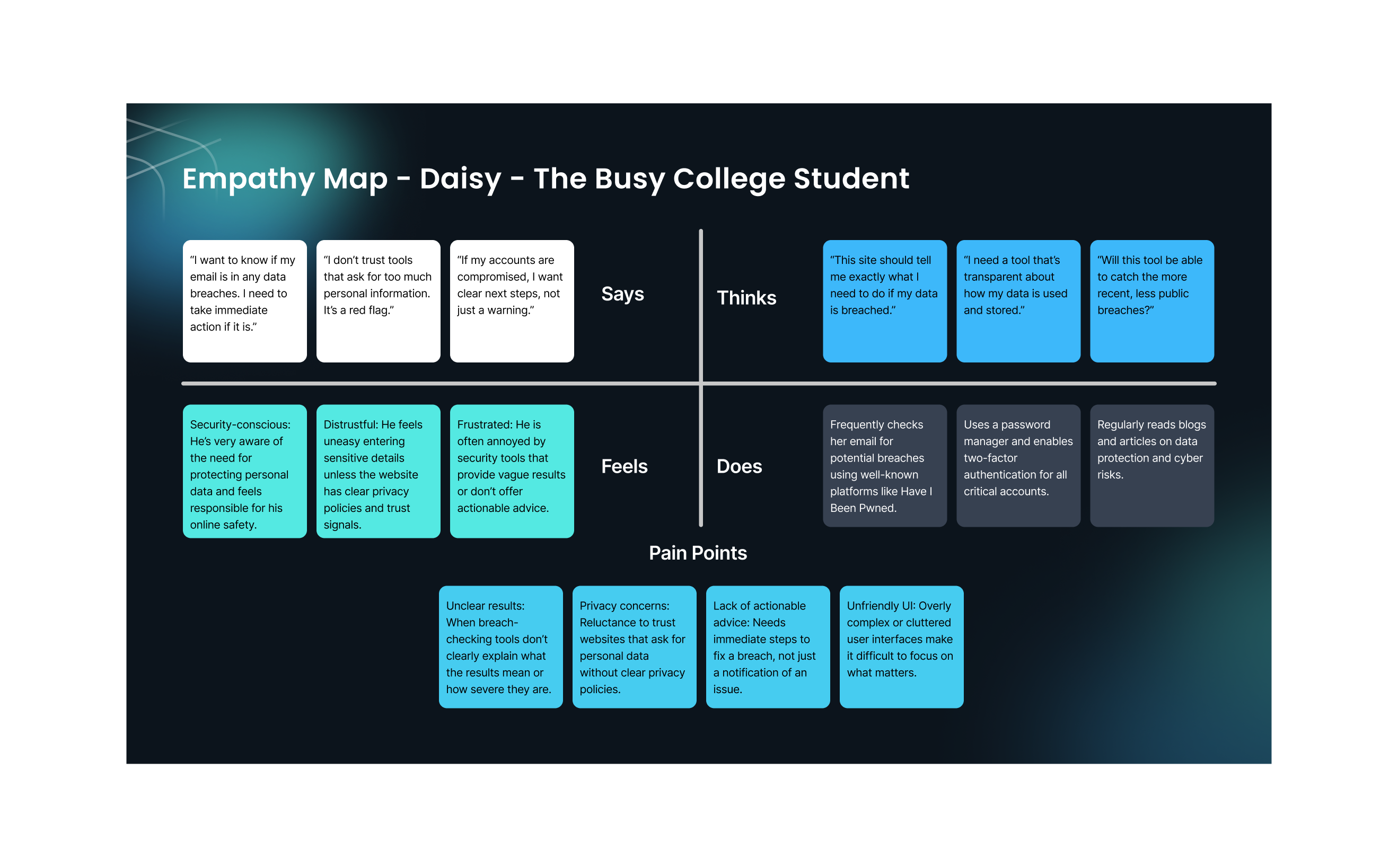
Darshan – The Mid-Level Professional

Basic Info:
- Name: Darshan Patel
- Age: 30
- Occupation: Marketing Manager
- Location: Bangalore, India
- Tech Proficiency: Advanced (Uses tech for work, personal, and daily tasks)
Background:
Darshan is a busy marketing manager at a mid-sized company. He is always online for work, using tools like Google Drive, LinkedIn, and his company’s CRM. Darshan is highly aware of cybersecurity risks, having witnessed colleagues’ accounts being compromised in the past. Though he uses strong passwords and two-factor authentication, he is still worried about breaches, especially after hearing about several large-scale hacks.
Goals:
- To check her email and phone number for potential breaches, particularly since she handles sensitive company data and communicates regularly with clients.
- Needs reliable, transparent security tools that don’t require too much time but give her peace of mind.
- Prefers having clear actions and recommendations for securing her accounts once a breach is found.
Pain Points:
- Doesn’t want to waste time on complex security tools: He needs something fast and efficient that doesn’t interrupt his day.
- Confusion around security terminology: Terms like “breach,” “leak,” and “hack” are often unclear to him, especially when he’s in a rush.
- Distrust of new websites: He’s hesitant to enter personal details unless the tool is widely known and trusted.
Technology Use:
- Device Preference: Primarily desktop (70%) and mobile (30%).
- App Usage: Heavy user of Google Workspace, social media for professional networking, and productivity apps.
- Cybersecurity Tools: Frequently uses password managers, VPNs, and regularly checks for breaches using popular services like Have I Been Pwned.
Behavioral Traits:
- Security-conscious and proactive about online risks.
- Will take time to read up on security recommendations or blogs.
- Hopes to stay ahead of risks to avoid business disruptions.
- Uses a combination of both free and paid tools for monitoring her security.
Insights
Key Design Opportunities
- Simplified Terminology: Offer clear definitions for security terms and step-by-step guidance for actions.
- Trust and Privacy: Include clear privacy policies, trust badges, and easy-to-understand disclaimers to address concerns.
- Clear Next Steps: After a breach check, provide users with actionable advice like “Change your password” or “Monitor your accounts.”
- Fast Feedback: Ensure the tool provides immediate, clear feedback after submitting a search.
- For Daisy, simplicity is key. The tool needs to be intuitive, mobile-first, and allow her to quickly check breaches with minimal steps. Educational tooltips or quick FAQs can help her understand what a breach means without overwhelming her with details.
- For Darshan, the tool must be trustworthy and efficient, with clear action steps if a breach is found. He values transparency, so privacy policies and a “no data storage” message are essential. He’s also likely to appreciate actionable security advice post-breach.
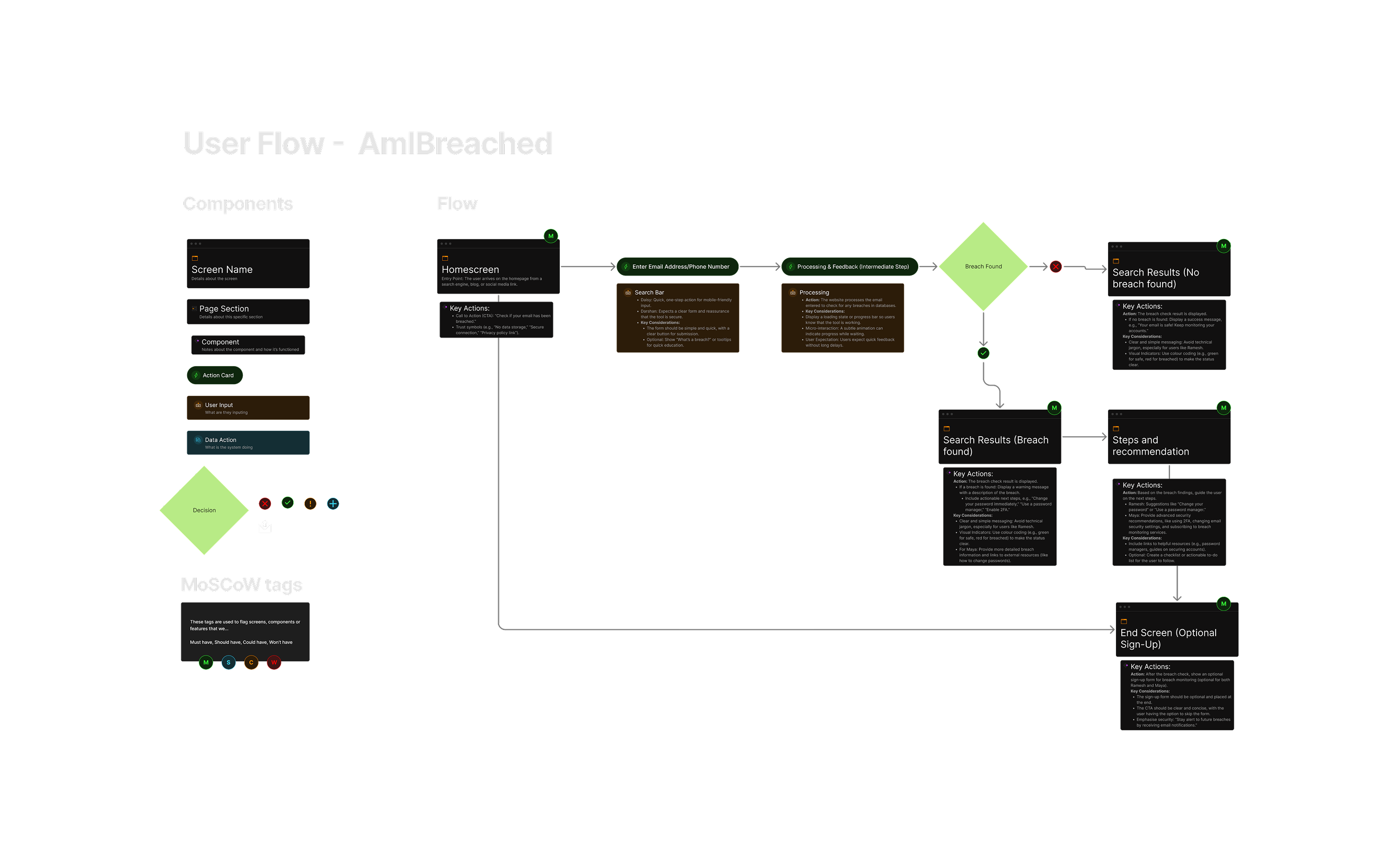
Key Flow Highlights
- Clear Instructions: Keep the CTA and actions straightforward, with minimal text or distractions.
- Reassurance: Provide users with trust badges and privacy policies at every major stage (email entry, results screen, next steps).
- User-Focused Results: Make sure results are actionable and easy to understand, catering to users’ varying technical knowledge (from Ramesh to Maya).
- Always follow up with concrete actions users can take (e.g., password change, security enhancements).
- Optional Sign-Up: Keep any form of sign-up or additional user engagement as optional, ensuring it doesn’t interrupt the primary breach-check flow.
Key Design Goals Reflected in IA
- Simplicity: Core action (email check) is upfront and immediate.
- Clarity: Separate paths for breached and non-breached outcomes.
- Trust: Transparent privacy practices highlighted.
- Guidance Clear resources and help for users regardless of outcome.
Prototyping and User Testing
- Interactive Prototype: We created an interactive prototype in Figma to simulate the user flow from the landing page to the results screen and beyond. The prototype allowed us to test:
- The efficiency of the flow (e.g., did users find the process quick and easy?).
- User reactions to breach notifications and the clarity of next steps.
- Mobile responsiveness and usability across different devices.
- User Testing: We conducted user testing with both Ramesh and Maya (our personas) and gathered feedback on the following:
- Ease of Use: Was the process simple and intuitive for users with varying technical knowledge?
- Trust and Security: Did the users feel confident in entering their email address and using the service?
- Actionability: Were the breach results clear and easy to understand? Did users know exactly what to do next?
- Key Findings:
- Both users appreciated the simplicity of the design and the quick feedback.
- Users like Daisy, who were less familiar with data security, needed clearer instructions on what to do after a breach.
- Users like Darshan wanted more detailed information and security best practices to secure their accounts after a breach.
- Trust symbols and clear privacy policies were critical for both personas.
Conclusion
Through this thorough and user-centered design process, we were able to create a simple, secure, and actionable experience for users of AmIBreached.com. The focus on clarity, trust, and actionable steps ensured that users could check their email for breaches and quickly take steps to secure their accounts. The iterative design process, based on user feedback and research, helped refine the experience and ultimately led to a final design that met the needs of both Daisy and Darshan.