Odin -
Internet Scanning Tool
Internet Scanning Tool
Introduction
ODIN.io is a threat-hunting platform that maps the entire internet, indexing billions of IPv4 hosts and petabytes of exposed data. Its target users are security analysts, threat researchers, red teams, and incident responders who need to:
- Discover vulnerabilities in assets they own or monitor.
- Investigate suspicious entities (IPs, domains, hashes, buckets).
- Perform recon on exposed infrastructure across the web and dark web.
-
CompanyCyble
-
Year2024
-
RoleProduct Designer
-
Product Link
Problem Statement
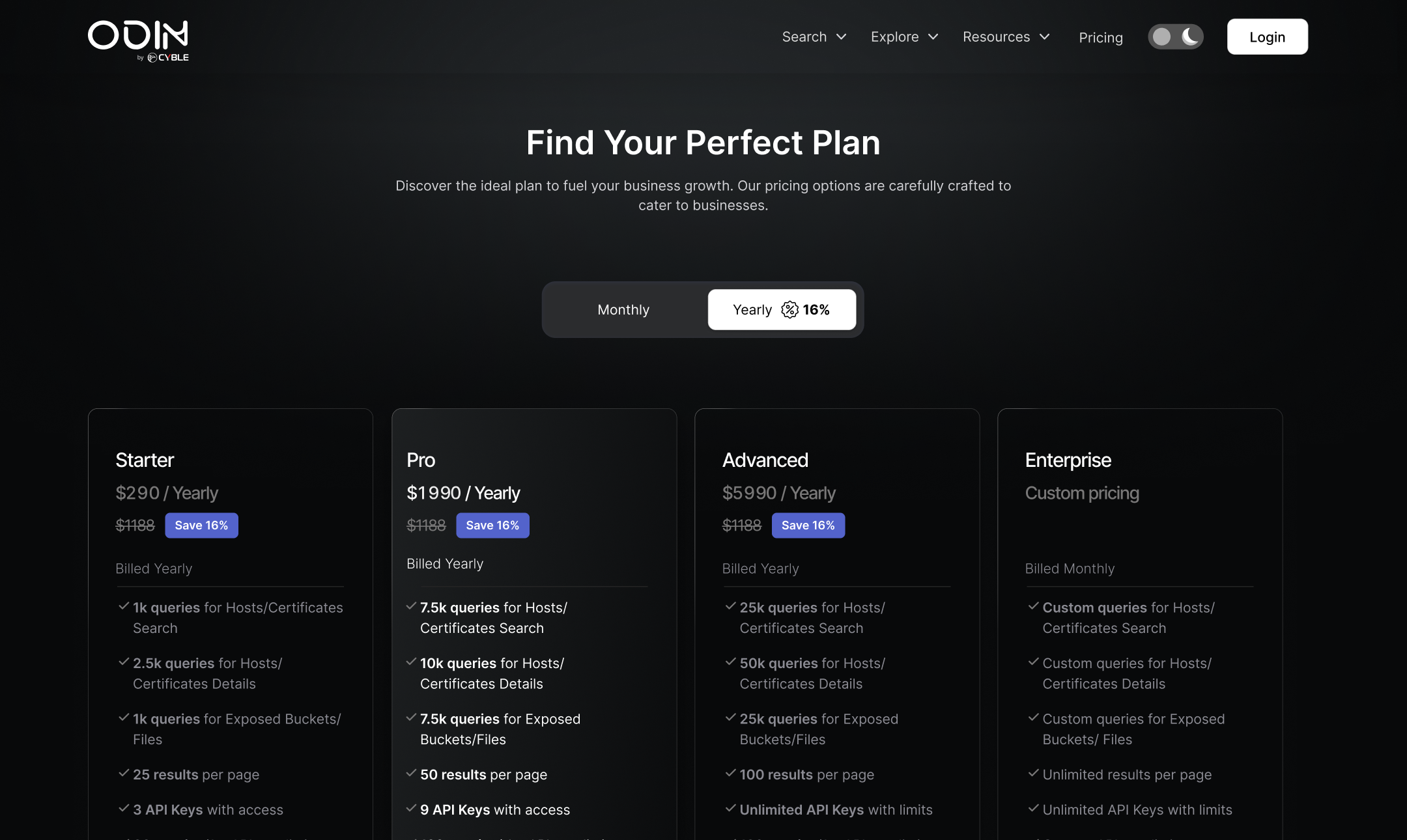
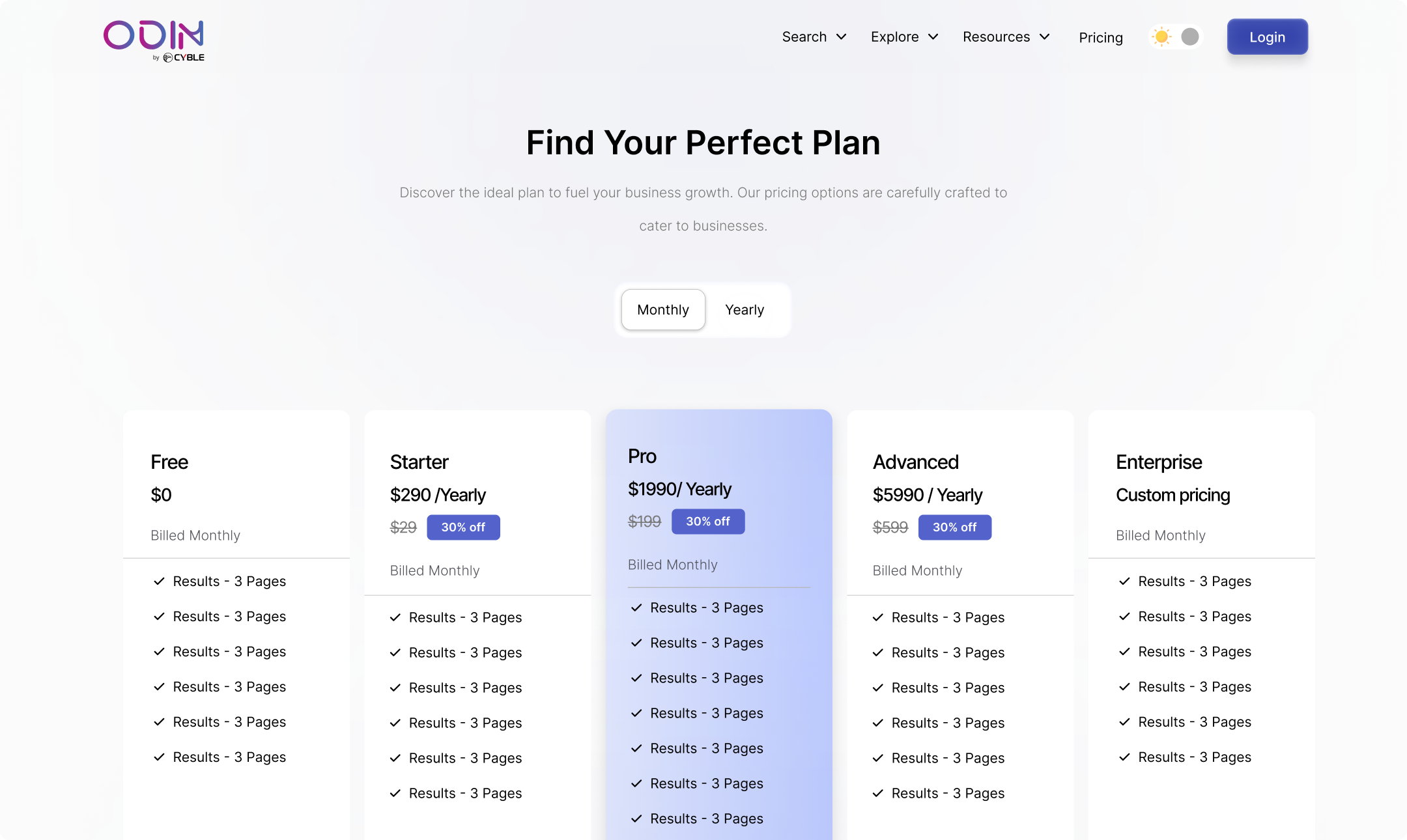
ODIN Search is a powerful open-source intelligence (OSINT) platform used by cybersecurity professionals to investigate digital assets, exposures, and indicators of compromise. Despite its technical robustness and access to rich datasets, users experience a steep learning curve and cognitive overload due to a query-only interface heavily reliant on Lucene syntax.
User research revealed that while expert users appreciate the control and depth Lucene offers, intermediate and novice users struggle to construct meaningful queries, navigate the interface, and interpret results efficiently. This disparity leads to inconsistent user experiences, decreased retention among new users, and reduced productivity for analysts under time pressure.
- Abandon searches due to failed syntax,
- Rely heavily on external documentation or community support,
- Miss out on critical insights hidden in less discoverable sections of the UI.
Additionally, the lack of visual hierarchy, intuitive filtering, and in-product guidance causes users to:
- Flexible for experts,
- Guided for beginners,
- And efficient for daily operational tasks.
In an increasingly time-sensitive and high-stakes threat detection environment, users need a search experience that is:
Core UX Problem
How might we redesign the ODIN search experience to support both novice and expert users—by improving discoverability, reducing friction in query construction, and enabling faster investigative pivots—without compromising the platform’s technical depth?
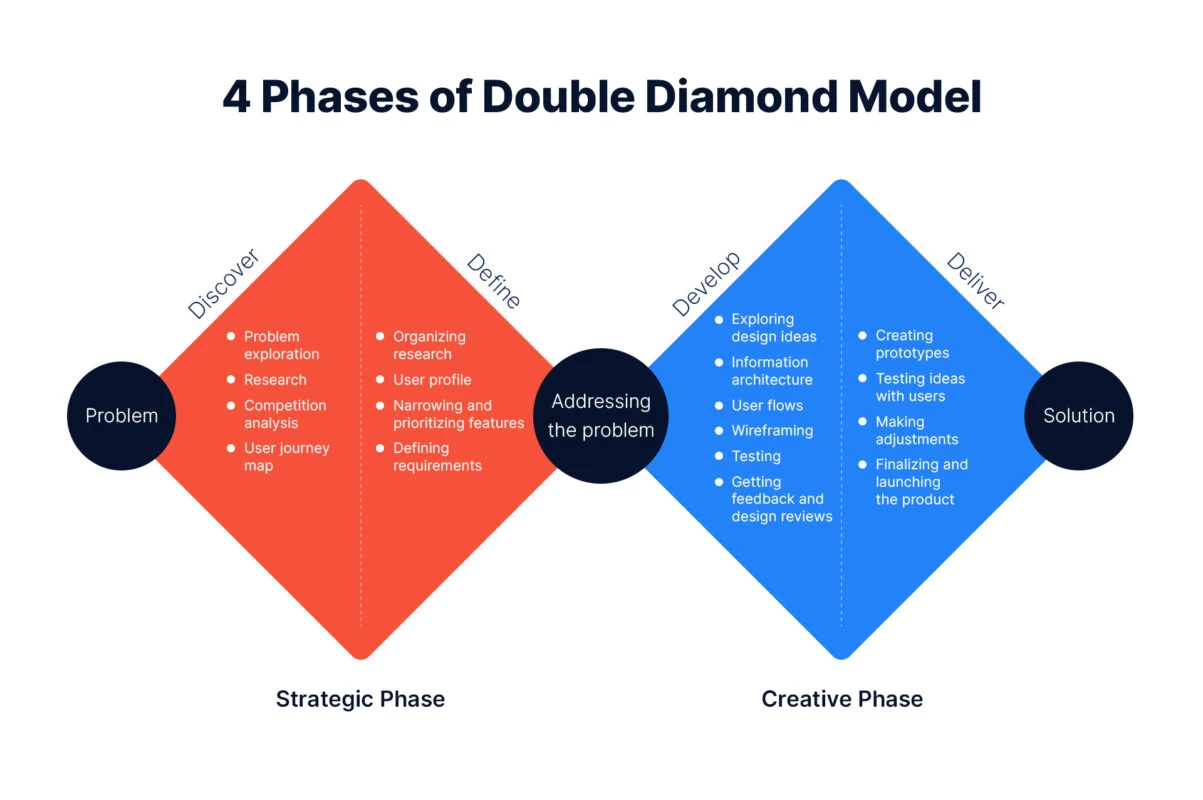
Framework: Double Diamond Design Process
1. Discover – Understanding the Problem
Goals:
- Identify user pain points in the search experience.
- Understand how users currently interact with ODIN.
Methods Used:
- User Interviews & Think-Aloud Protocol
Observed how cybersecurity professionals search for IPs/domains, their thought process, and where friction occurred. - Heuristic Evaluation
Applied usability heuristics to assess flaws in the search interface. - Analytics & Heatmap Tools
Used Google Analytics and Hotjar to track drop-offs, click patterns, and session recordings. - Competitor Analysis
Reviewed platforms like Shodan, BinaryEdge, LeakIX, and ZoomEye to benchmark features. - User Surveys
Quantified user frustration and expectations for filters, sorting, and speed.
2. Define – Framing the Core Problems
Activities:
- Affinity Mapping
Clustered data from research into themes: usability issues, filter confusion, inconsistent result layout. - Persona Creation
Created profiles for two key users: a Pen Tester and a Threat Analyst. - Empathy & Journey Mapping
Tracked emotions, pain points, and goals at each search stage.
Problem Statements“Users are unable to efficiently find relevant information due to lack of filtering, unclear result labeling, and poor information hierarchy.”
3. Develop – Ideating Solutions
Activities:
- Ideation Workshops
Brainstormed solutions like advanced filters, collapsible result cards, and interactive search previews. - Wireframes & Low-Fidelity Prototypes
Sketched new layouts for search results with better hierarchy and customization. - Design Reviews
Collaborated with engineers and stakeholders to align on feasibility and user impact.
4. Deliver – Testing & Iterating Final Designs
Activities:
- High-Fidelity Prototypes
Created using Figma. Included advanced filters, pinned searches, preview cards, and improved data layout. - Usability Testing
Measured task success, completion times, and user satisfaction.
Conducted A/B tests comparing old vs new layouts. - Iterative Refinements
Incorporated feedback to finalize the MVP-ready design. - Improved engagement & search efficiency
- Better clarity, fewer drop-offs, and increased satisfaction
- Used in pitch that helped raise $24M in funding
- Outcome:
User Interview
Objective
To understand the current user experience, pain points, and expectations of cybersecurity professionals using ODIN’s search platform, especially in context of dark web scanning and information gathering.
Participant Profile
We interviewed 6 participants across different cybersecurity roles:
-
RoleThreat Intelligence AnalystSOC AnalystCybersecurity ResearcherIncident ResponderSecurity Consultant
-
Experience4 years2 years5 years3 years7 years
-
Primary Use of ODINTracking breaches and exposed assetsInvestigating suspicious IPs/domainsData enrichment and asset discoveryRoot cause analysis and dark web checksAudit and vulnerability assessments
Key Questions Asked
- How often do you use ODIN? For what purpose?
- What are your thoughts on the current search interface?
- Can you walk me through your recent experience using ODIN to investigate a threat?
- What features do you use most frequently? Which ones do you ignore or don’t understand?
- What frustrates you the most while using the platform?
- Are there any tools you prefer over ODIN? If yes, why?
- What’s one thing you wish ODIN could do better?
Insights Gathered
- Search Bar Limitations: Users found the search bar too generic and lacking advanced filters. Many wanted an “autocomplete” or syntax suggestion feature like Shodan.
- Result Overload: The search results often lacked prioritization or relevance, especially when scanning large CIDR blocks or domains.
- Lack of Contextual Metadata: Many users expected clearer tags, timestamps, and source validation indicators to make sense of the results.
- Slow Performance on Bulk Queries: Users felt delays when performing deep scans or querying multiple fields simultaneously.
- Missing Visual Clarity: Users found the data tables and UI cluttered, especially when switching between tabs like IP, URL, Paste, etc.
- Desire for Saved Searches: Professionals wanted to bookmark or save complex queries for reuse, especially during incident response workflows.
Quote Highlights
“I often forget what I searched earlier because there’s no history or saved state. That’s frustrating during long investigations.”
— Threat Intel Analyst, 4 yr
“I like how much data ODIN collects, but the UI doesn’t guide me on what matters most in the results.”
— Security Consultant, 7 yrs
Affinity Mapping
After conducting user interviews, we organized the insights into clusters to identify recurring themes, pain points, and opportunities for design improvement. Using digital sticky notes in FigJam, we grouped similar responses to form clear categories.
Grouped Insights
- Search Experience & Efficiency
- “I don’t always know what syntax to use.”
- “Auto-suggestions would save me time.”
- “Search feels flat — everything looks the same.”
- “Search results lack hierarchy or sorting options.”
- Data Interpretation Challenges
- “I get tons of results but can’t figure out what’s most important.”
- “It’s hard to tell which sources are trustworthy.”
- “Timestamp clarity is missing — when was this leaked?”
- User Interface & Visual Clarity
- “Feels like information overload.”
- “Switching between tabs breaks my flow.”
- “Table view is dense and hard to scan quickly.”
- Workflow Interruptions
- “I often lose my query and have to redo the search.”
- “No way to bookmark or save searches — very frustrating.”
- “I want a recent searches panel.”
- Comparison with Competitors
- “Shodan gives me cleaner results.”
- “ZoomEye has better filters for specific queries.”
User Persona
Based on the interview and affinity map, we crafted user personas to represent key user archetypes. These personas guide our design decisions by keeping user needs front and center.
Alex – The Threat Intel Analyst

Basic Info:
- Name: Alex
- Age: 32
- Occupation: Threat Intel Analyst
- Location: California, USA
- Experience: 4 Years
Goals:
- Identify exposed data quickly during investigations.
- Save and revisit frequent search queries.
Frustrations:
- No saved query history.
- Results feel unprioritized and overwhelming.
Quote
“I need to make quick decisions based on data, but ODIN slows me down with too much noise.”
Priya – The Security Researcher

Basic Info:
- Name: Priya
- Age: 29
- Occupation: The Security Researcher
- Location: California, USA
- Experience: 5 Years
Goals:
- Use ODIN for deep reconnaissance and enrichment.
- Export clean datasets to compare with internal tools.
Frustrations:
- Missing advanced filtering options.
- UI doesn’t scale well with deep or complex queries.
Quote
“The potential is great, but I struggle to extract usable insights from the raw data.”
User Journey Map
We mapped out the end-to-end journey of a typical user (Raj, our Threat Intel Analyst persona) interacting with ODIN’s search feature to uncover critical moments of friction and opportunity.
Based on our research and mapping, we identified the core user problem:Security analysts using ODIN’s search feature struggle to extract meaningful insights quickly due to a lack of guidance, overwhelming results, and the inability to revisit or organize search queries efficiently.
How Might We (HMW) Questions
To fuel ideation, we reframed the problems into design opportunities:
- How might we help users build effective queries without needing to remember complex syntax?
- How might we present results with visual hierarchy to help users prioritize data faster?
- How might we reduce context switching while exploring detailed records?
- How might we enable users to save, manage, or revisit their search workflows easily?
- How might we make ODIN feel more like a power tool and less like a raw data dump?
Competitor Review
To evaluate ODIN’s position in the threat intelligence landscape, we conducted a competitive UX review of four major platforms: Shodan, BinaryEdge, ZoomEye, and LeakIX. The goal was to understand how these tools support search workflows and identify UX best practices ODIN could adopt or improve upon.
Key Takeaways
- Most competitors fail at onboarding: Advanced users thrive, but new users struggle.
- Complex filters ≠ intuitive search: Guidance, not just power, makes a search tool usable.
- Visual overload is common: The market lacks clean interfaces that guide focus effectively.
Business Impact Analysis
The objective of the UX redesign of ODIN’s search experience was to streamline complex search tasks, reduce friction, and enhance usability, particularly for cybersecurity professionals relying on precision and efficiency. The improvements aimed to increase user satisfaction, reduce drop-off, and ultimately support the company’s revenue growth by improving retention and feature adoption.
-
MetricCustomer Satisfaction Score (CSAT)Net Promoter Score (NPS)Support Tickets (related to search issues)Onboarding Time for New Users
-
ResultIncreased from 68 to 88 after redesign.Improved from 24 to 41.Decreased by 40%.Reduced by 35% due to simplified workflows.
-
FactorUser ConversionRevenue AttributionChurn Reduction
-
OutcomeClearer value proposition in UX increased free-to-paid conversions by 18%.Enhanced user flows led to a 12% increase in feature engagement related to premium tools.Lower friction and better UX reduced churn by 15%.Reduced by 35% due to simplified workflows.
Ideation & Design Principles
Based on research insights, competitor gaps, and user pain points, I focused on crafting design solutions that balance functionality, clarity, and efficiency—especially for threat analysts working under pressure.
- Reduce cognitive overload during search and result analysis.
- Empower all users (novices to experts) with accessible query-building tools.
- Streamline navigation and remove dead-ends or friction points in the workflow.
- Improve scannability and prioritization in search results.
- Facilitate continuity through saved searches and reusable sessions.
Design Goals
UX Principles Applied
-
PrincipleVisual HierarchyProgressive DisclosureRecognition over RecallConsistency & StandardsFeedback & VisibilityError PreventionUser Control & Freedom
-
Experience4 years2 years5 years
-
Application in ODINClear prioritization of search results using weight, contrast, and whitespace.Advanced filters and metadata shown contextually, reducing interface clutter.Auto-suggestions, saved queries, and history enhance user speed and accuracy.Unified design language across modules (search, filter, result viewer) with familiar iconography.Live query preview, loading indicators, and result summaries to keep users informed at every step.Query validation, filter dependencies, and helpful tooltips to prevent misconfigured searches.Undo changes, clear filters, and edit queries with minimal disruption.
- Competitive Advantage: The improved UX made ODIN more competitive compared to tools like Shodan, BinaryEdge, and ZoomEye.
- Brand Perception: A polished and intuitive interface improved the perception of ODIN as a professional-grade, user-centric platform.
- Scalability: Modular improvements laid the groundwork for scalable UX updates across other product features.
Strategic Impact
Conclusion
The redesign of ODIN’s search experience was driven by a deep understanding of user behavior, pain points, and expectations within a technical and data-heavy environment. Through user interviews, usability testing, and competitor benchmarking, we identified critical friction points in the search journey and addressed them with targeted UX solutions — including smart suggestions, query assistance, improved result hierarchy, and contextual views.
The outcome was not only a significant improvement in user satisfaction and search efficiency but also measurable business impact: higher conversion rates, reduced churn, and fewer support tickets. The new experience empowers users to explore cybersecurity data with clarity, speed, and confidence — aligning usability with the power of ODIN’s capabilities.
This case study highlights how user-centered design, when combined with data-driven decisions, can transform a powerful but complex tool into an accessible and engaging product that drives growth.